While acknowledging API opportunities, you can’t skip the topic of API security risks. After all, APIs are one of the most significant cyberattack vectors.
In one survey, 41% of businesses reported experiencing a recent API security incident. Of those businesses that noted an incident, 63% dealt with a data breach or loss.
Consider what a data breach means for a bank or healthcare operator. With what’s on the line, getting in front of API security risks is critical. Doing so starts with an understanding of the biggest dangers for APIs.
A top 10 list of API security risks
API vulnerabilities constantly evolve. The Open Web Application Security Project (OWASP) releases an updated top 10 list of API security risks every year or two. Here’s their most recent breakdown:
- Broken object-level authorization: Insecure coding practices can let users access other user data.
- Broken authentication: Poor password implementation, for instance, can compromise authentication tokens.
- Broken object property level authorization: Incorrect user permissions allow unwanted property access.
- Unrestricted resource consumption: An attacker can overwhelm an API and degrade service.
- Broken function level authorization: Unclear admin and user functions increase vulnerabilities.
- Unrestricted sensitive data flow access: Users can perform sensitive operations and access data.
- Server-side request forgery: Attackers can coerce applications without user-supplied URI validation.
- Security misconfiguration: Improper API configuration opens the door to risks.
- Improper inventory management: A lack of control over APIs increases security gap risks.
- Unsafe consumption of APIs: Trusting external API data can lead to attacks and leaks.
Read an in-depth analysis of each vulnerability and how to remediate them here.
Steps you can take to keep your APIs secure
There isn’t one surefire way to keep your APIs safe. But there are a lot of measures you can take to reduce the odds of exposure.
The conversation begins with the design and development of your APIs. By taking an API-first approach, security becomes less of an afterthought. Instead, security becomes an integral part of the design and planning process. This practice helps you establish secure configurations and address any issues early on.
API Security Tools and Best Practices
Adopting a zero-trust security framework is also recommended. This framework operates under the “never trust, always verify” principle. It recommends using multi-factor authentication and access controls with the least privilege.
It’s also a matter of monitoring API activities so you can detect and respond to potential security threats without delay.
Axway’s 2024 State of Enterprise API Maturity report found that most enterprises struggle with having sufficient visibility over all their APIs.
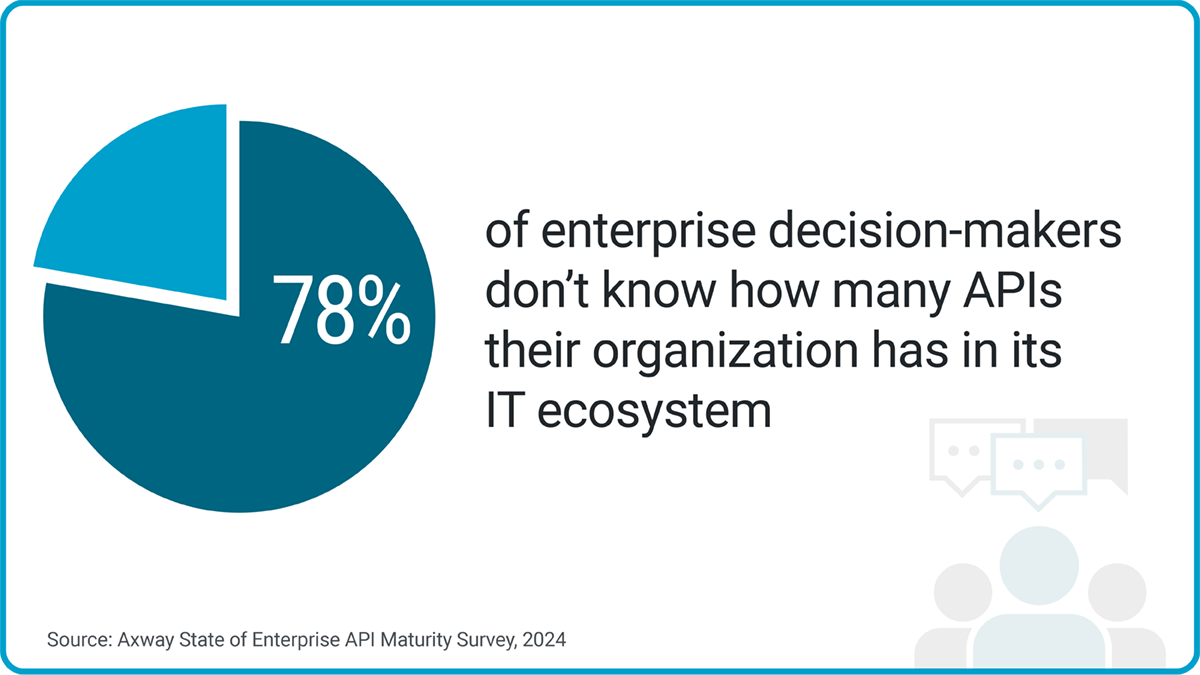
To further guarantee API governance, maintain an updated inventory of all APIs. That way, you can ensure all your APIs have secure endpoints and the proper access controls.
In fact, there was clear consensus on this point in the above-mentioned survey: 95% of IT and LOB decision-makers agree that a centralized API catalog would improve the governance of APIs.
From this catalog, you can identify any unused or deprecated APIs to decommission. Doing so will reduce the number of vulnerable endpoints.
Dive Deeper Into API Security Governance
The following video gives a very quick overview of 12 best practices; dive deeper into the topic with this blog on API security best practices.
What about when you open up APIs for external consumption?
Like many organizations, you’re likely interested in API monetization. But when you open this door, how do you ensure your APIs stay secure?
Amplify Engage is built upon a true federated API management platform. With this platform, you can:
- Discover any unmanaged APIs within your organization
- Curate and select which APIs to make available in your marketplace
- Access prebuilt security policies, which you can customize as needed
Amplify Engage offers the building blocks and governance to keep APIs secure. Without disrupting the consumer experience, you can create a secure infrastructure. It’s a foundation you can trust to support API monetization.
Explore how Amplify Engage is an API portal built for battle.


